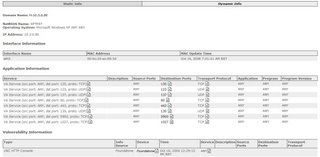
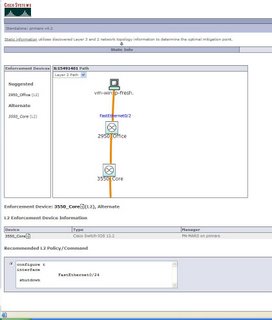
Netflow is a Cisco technology, that supports monitoring network and is supported on all basic IOS images.
Netflow is an efficient method of monitoring high volumes of traffic compared to traditional SYSLOG and SNMP methods. To receive comparable syslog data from a firewall device, the syslog logging level on the firewall would need to be set to DEBUG.
CS-MARS uses NetFlow Version 5 or Version 7. Ideally Netflow should be collected from the Core and Distribution switches in your network.
Netflow data enables MARS to identify anomalies by profiling typical data flows across your network. This allows MARS to detect day-zero attacks, including worm outbreaks.
MARS uses NetFlow data and Firewall traffic logs to
1. Profile the network usage - Statistical profiling takes between four days and two weeks for a MARS appliance to complete.
2. Detect statistically significant anomalous behavior and traffic flows (from computed baseline) and creates incidents in response to them.
3. Correlate anomalous behavior to attacks and other events reported by Network IDS systems.
The NetFlow data and Firewall traffic logs are treated uniformly since they both represent traffic in an enterprise network.
After getting inserted into a network, MARS learns the network usage for a few days. Then it switches to a detection mode where it looks for statistically significant behavior, e.g. the current value exceeds the mean by 2 to 3 times the standard deviation.
CS-MARS profiles the network at a detailed level and keeps a profile of top combinations of flows learned and packets exchanged for every hour, every day of the week.
By default MARS does not store the NetFlow records in the database because of the high data volume, although MARS can be configured to do so.
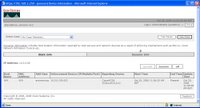
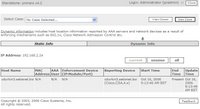
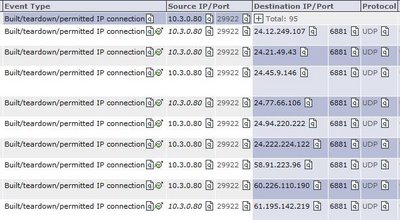
Upon detecting an anomalous behavior, MARS starts to dynamically store the full NetFlow records for the anomalous (host, port) - thus the full context of a security incident, e.g. the infected source,destination etc. is easily available to the administrator.
CS-MARS can be configured to profile hosts that belong to a set of known valid networks. This reduces MARS memory usage.
Upon detecting an anomalous behavior, CS-MARS starts to dynamically store the full NetFlow records for the anomalous activity. This intelligent collection system provides all the information that a security analyst needs and does not overburden CPU and disk resources.
MARS provides built-in rules for automatically correlating anomalous behavior with attacks reported by Network IDS systems - such a rule can easily capture a successful attack since a compromised host is likely to exhibit anomalous Network DoS behavior of the form
• Sending too many e-mails containing a worm
• Sending excessive traffic on a particular port looking for additional systems to compromise
IE, say that CS-MARS learns that most connections to and from a server in your environment are made over ports 137, 138, and 139. Then suddenly that server makes multiple outbound port 25 connections through the default gateway. CS-MARS would trigger a "mass-mailing worm" incident to notify the operators of the change in behavior.
Even without a Network IDS system in place, a host compromised by an unknown attack is highly likely to exhibit anomalous behavior of the form described above and hence will be easily detected by the MARS Appliance.
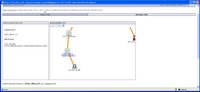
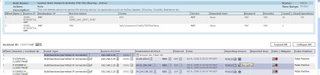
CS-MARS uses NetFlow and Firewall Log information to graphically depict port-level activity on your network using a graph that measures protocol connections over time.
CS-MARS Activity: All Events and NetFlow Chart
Netflow is an efficient method of monitoring high volumes of traffic compared to traditional SYSLOG and SNMP methods. To receive comparable syslog data from a firewall device, the syslog logging level on the firewall would need to be set to DEBUG.
CS-MARS uses NetFlow Version 5 or Version 7. Ideally Netflow should be collected from the Core and Distribution switches in your network.
Netflow data enables MARS to identify anomalies by profiling typical data flows across your network. This allows MARS to detect day-zero attacks, including worm outbreaks.
MARS uses NetFlow data and Firewall traffic logs to
1. Profile the network usage - Statistical profiling takes between four days and two weeks for a MARS appliance to complete.
2. Detect statistically significant anomalous behavior and traffic flows (from computed baseline) and creates incidents in response to them.
3. Correlate anomalous behavior to attacks and other events reported by Network IDS systems.
The NetFlow data and Firewall traffic logs are treated uniformly since they both represent traffic in an enterprise network.
After getting inserted into a network, MARS learns the network usage for a few days. Then it switches to a detection mode where it looks for statistically significant behavior, e.g. the current value exceeds the mean by 2 to 3 times the standard deviation.
CS-MARS profiles the network at a detailed level and keeps a profile of top combinations of flows learned and packets exchanged for every hour, every day of the week.
By default MARS does not store the NetFlow records in the database because of the high data volume, although MARS can be configured to do so.
Upon detecting an anomalous behavior, MARS starts to dynamically store the full NetFlow records for the anomalous (host, port) - thus the full context of a security incident, e.g. the infected source,destination etc. is easily available to the administrator.
CS-MARS can be configured to profile hosts that belong to a set of known valid networks. This reduces MARS memory usage.
Upon detecting an anomalous behavior, CS-MARS starts to dynamically store the full NetFlow records for the anomalous activity. This intelligent collection system provides all the information that a security analyst needs and does not overburden CPU and disk resources.
MARS provides built-in rules for automatically correlating anomalous behavior with attacks reported by Network IDS systems - such a rule can easily capture a successful attack since a compromised host is likely to exhibit anomalous Network DoS behavior of the form
• Sending too many e-mails containing a worm
• Sending excessive traffic on a particular port looking for additional systems to compromise
IE, say that CS-MARS learns that most connections to and from a server in your environment are made over ports 137, 138, and 139. Then suddenly that server makes multiple outbound port 25 connections through the default gateway. CS-MARS would trigger a "mass-mailing worm" incident to notify the operators of the change in behavior.
Even without a Network IDS system in place, a host compromised by an unknown attack is highly likely to exhibit anomalous behavior of the form described above and hence will be easily detected by the MARS Appliance.
CS-MARS uses NetFlow and Firewall Log information to graphically depict port-level activity on your network using a graph that measures protocol connections over time.
CS-MARS Activity: All Events and NetFlow Chart
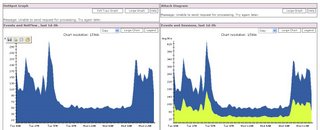
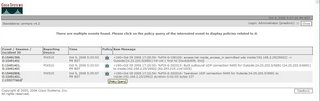
 And you can run queries too.
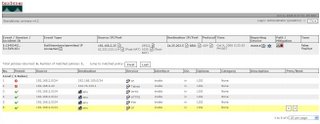
And you can run queries too.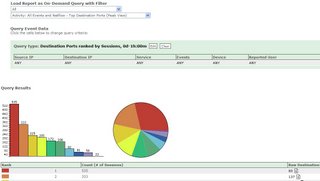 As can be seen in the picture MARS has reported huge deviations from typical port 80 activity. This would obviously be more interesting with a day zero worm or virus , using a non statndard port, but this is an example of behaviorally profiling port activity.
As can be seen in the picture MARS has reported huge deviations from typical port 80 activity. This would obviously be more interesting with a day zero worm or virus , using a non statndard port, but this is an example of behaviorally profiling port activity.Often when these malicious programs are released, they do not contain names or have detection signatures for them. Your organization's only defense against detecting and mitigating day-zero attacks at a network level is to use CS-MARS. Firewall data and NetFlow information give you this unique capability.
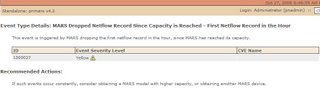
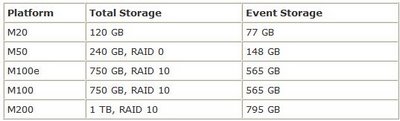
A word of warning though about Netflow. Too much will increase the CPU requirements of your MARS Appliance. MARS does though have a couple of warning alerts, can can give you an indication you have undersized the right appliance for your network. See below.