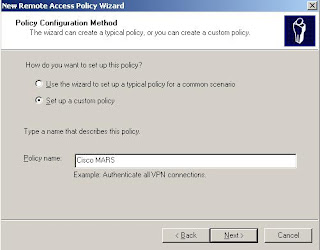
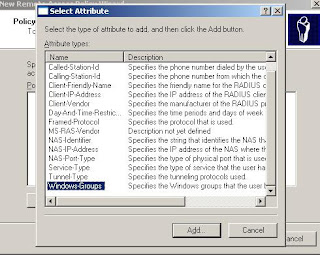
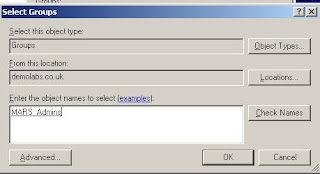
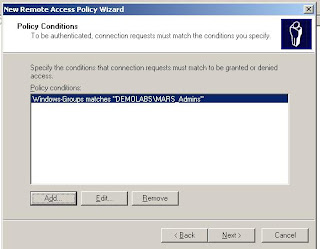
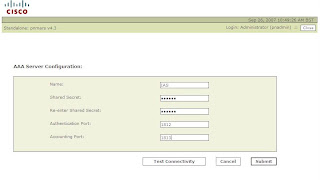
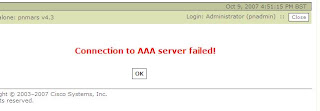
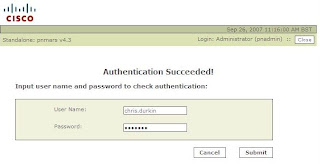
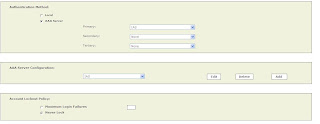
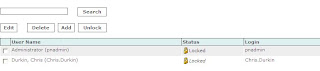
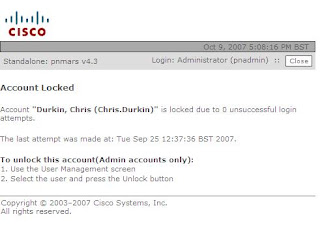
Release Notes for Cisco Security MARS Appliance 4.3.2
Release Notes for Cisco Security MARS Appliance 5.3.2
As mentioned the other day, the major difference between the 2 release codes, is Wireless Controller support in 5.3.2, but not 4.3.2.
"Cisco Secure MARS 5.3. x supports the collection, parsing, and analysis of SNMP security traps generated by Cisco Wireless Controller, version 4.x. devices. In addition, MARS includes this event data in new and existing reports and rules. Support for Cisco Wireless Access Points is enabled via Cisco Wireless LAN Controller, v. 4.1.171.0, which forwards SNMP traps to the MARS Appliance for processing."
Theres also the usual updated Vendor Signatures...
 The other new Enhancements are shown below, ripped from the release notes....
The other new Enhancements are shown below, ripped from the release notes....
Theres also the usual updated Vendor Signatures...
 The other new Enhancements are shown below, ripped from the release notes....
The other new Enhancements are shown below, ripped from the release notes....•New Activate Button and Activation Scheduler
The Activate button now displays red when a configuration change requires activation. Previously, there was no change in the display of the button. Additionally, a scheduler daemon can be configured from the GUI to automatically execute activations.
•Support for Custom Signature Definitions in Cisco IPS.
Cisco IPS 6.0 enables you to define custom signatures for Cisco IPS devices. In 5.3.2, you can map that signature to a MARS event type so that an inspection rule in MARS fires when that signature is detected. To do so, you must define an XML file that maps between the custom signature and the event type in MARS as well as manually update the Local Controller from the Admin > System Setup > IPS Signature Dynamic Update Settings page.
•Global Controller-to-Local Controller Communication Enhancements.
Enhancements include the following:
–Topology-sync performance improvement
–Report Results performance
–Incidents/Firing Events performance
•Enhanced Cisco Device Support:
–IOS 12.3, 12.4(11) T-T4
–PIX and ASA 7.0.7, 7.2.2, 7.2.3, and 8.0.
–Cisco IPS 6.0 (IDSM/2, IPS 4270, and ASA-IPS SSM 10/20 support)
–FWSM 3.1.4, 3.1.6, and 3.2
•Enhanced 3rd-Party Device Support.
–Juniper IDP 3.x via IDP management server (3.0, 3.1)
–Juniper IDP 4.x via NSM (4.0, 4.1)
–Symantec AntiVirus 10.x (10.1, 10.2)
The Activate button now displays red when a configuration change requires activation. Previously, there was no change in the display of the button. Additionally, a scheduler daemon can be configured from the GUI to automatically execute activations.
•Support for Custom Signature Definitions in Cisco IPS.
Cisco IPS 6.0 enables you to define custom signatures for Cisco IPS devices. In 5.3.2, you can map that signature to a MARS event type so that an inspection rule in MARS fires when that signature is detected. To do so, you must define an XML file that maps between the custom signature and the event type in MARS as well as manually update the Local Controller from the Admin > System Setup > IPS Signature Dynamic Update Settings page.
•Global Controller-to-Local Controller Communication Enhancements.
Enhancements include the following:
–Topology-sync performance improvement
–Report Results performance
–Incidents/Firing Events performance
•Enhanced Cisco Device Support:
–IOS 12.3, 12.4(11) T-T4
–PIX and ASA 7.0.7, 7.2.2, 7.2.3, and 8.0.
–Cisco IPS 6.0 (IDSM/2, IPS 4270, and ASA-IPS SSM 10/20 support)
–FWSM 3.1.4, 3.1.6, and 3.2
•Enhanced 3rd-Party Device Support.
–Juniper IDP 3.x via IDP management server (3.0, 3.1)
–Juniper IDP 4.x via NSM (4.0, 4.1)
–Symantec AntiVirus 10.x (10.1, 10.2)