MARS can be configured to do Policy Table Lookups from Cisco Security Manager.
What does this mean? Well, when your MARS box receives a syslog from a Cisco PIX/ASA/FWSW/IOS device, and this event is sessionized, you will get a new "Security Manager Policy Table Lookup Icon" in the Reporting Device column..
If we click on this icon, then we can invoke a query to our Cisco Security Manager installation, and this will identify the access rule of the device, which created the incident.
Obviously looking at the raw event messages from the device would show the access-list, but not the particular entry in that list.
Prerequisities for Policy Table Lookup
MARS Local Controller running 4.2.1 or above
Cisco Security Manager v3.0.1 or above
See the example below...
We have a Cisco PIX being managed via the Security Manager, and have created some noddy access rules.
What does this mean? Well, when your MARS box receives a syslog from a Cisco PIX/ASA/FWSW/IOS device, and this event is sessionized, you will get a new "Security Manager Policy Table Lookup Icon" in the Reporting Device column..
If we click on this icon, then we can invoke a query to our Cisco Security Manager installation, and this will identify the access rule of the device, which created the incident.
Obviously looking at the raw event messages from the device would show the access-list, but not the particular entry in that list.
Prerequisities for Policy Table Lookup
MARS Local Controller running 4.2.1 or above
Cisco Security Manager v3.0.1 or above
See the example below...
We have a Cisco PIX being managed via the Security Manager, and have created some noddy access rules.

We have defined the CSM as a reporting device in MARS, and we are ready to go!
1) Log onto MARS as the Admin or Security Analyst Role
2) Identify the Incident
1) Log onto MARS as the Admin or Security Analyst Role
2) Identify the Incident
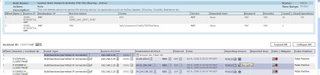
3) Click the Security Manager Policy Query Icon in the Reporting Field, to invoke the Cisco Security Manager Policy Table Lookup.
It is important to note here, that there are 3 pop-ups that can now appear, depending if there are mulitple events/devices that match the criteria.
a) Multiple Events Window (Shown) - Lists all the Security Manager device events, in the session
b) Multiple Devices Window - Lists all the matching SM devices that meet the criteria available to MARS
c) The Policy Table Window, shown when there is only one event, and a unique SM device indentifed.
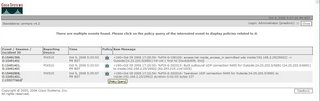
It is important to note here, that there are 3 pop-ups that can now appear, depending if there are mulitple events/devices that match the criteria.
a) Multiple Events Window (Shown) - Lists all the Security Manager device events, in the session
b) Multiple Devices Window - Lists all the matching SM devices that meet the criteria available to MARS
c) The Policy Table Window, shown when there is only one event, and a unique SM device indentifed.
 4) Finally the Lookup Table is shown, and as can be seen the Access Rule on the device has been identified.
4) Finally the Lookup Table is shown, and as can be seen the Access Rule on the device has been identified.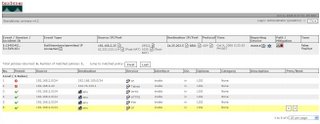
5) Finally we are offered advice on Mitigation, if we click the button, but remember the devices in CSM are Layer3 devices, so we cannot PUSH the configs. Any changes would need to be done MANUALLY on the device or via CSM.
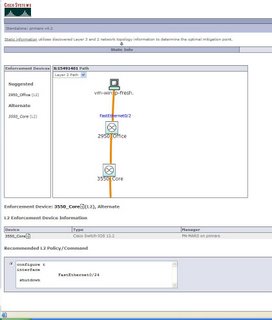
Change Management i think its called!







4 comments:
Hi, Can this be done with Cisco Security Device Manager, the freebie as well?
Tarik
Hi Tarik
No it cannot.
This feature is only available with the Cisco Security Manager Package.
See Below...
http://www.cisco.com/en/US/products/ps6498/index.html
Do you know how to demostrate the attack or incident for the policy table lookup? What i mean is create an incident and demostrate the policy table lookup.
Have a look on www.demolabs.co.uk, there is a demo showing that.
Post a Comment