The Payment Card Industry (PCI) Data Security Standard is applicable to all enterprise, SMB, and retail organizations that handle credit card transactions. Businesses of all sizes are responsible for complying with the PCI Data Security Standard.
Any company that stores, processes, or transmits credit card information is required to comply with PCI. The PCI standard was created by major credit card companies VISA and MasterCard. These companies have specific programs, such as VISA CISP and MasterCard SDP, which are based on the PCI standard. Other credit card companies have adopted the PCI Data Security Standard as well, such as American Express, Diners Club, and Discover.
How Can Cisco MARS help with complying with the PCI Data Security Standard?
MARS helps to meet some of the criteria needed. There are a couple of Requirements in the PCI Draft, namely Requirements 10 and 11, that MARS can provide a solution for.
I have detailed the PCI Requirements below, and reproduced Cisco views of how it meets those requirements, (with some sections relating to MARS plus A.N.Other Cisco Product to meet the requirement)
Links to the Cisco Website, and some great Whitepapers are also provided below..
Regularly Monitor and Test Networks
PCI Requirement 10: Track and monitor all access to network resources and cardholder data.
Logging mechanisms and the ability to track user activities are critical. The presence of logs in all environments allows thorough tracking and analysis if something goes wrong. Determining the cause of a compromise is difficult without system activity logs.
Sub-requirements:
10.1 Establish a process for linking all access to system components (especially those done with administrative privileges such as root) to an individual user.
10.2 Implement automated audit trails to reconstruct the following events, for all system components:
10.2.1 All individual user accesses to cardholder data
10.2.2 All actions taken by any individual with root or administrative privileges
10.2.3 Access to all audit trails
10.2.4 Invalid logical access attempts
10.2 5 Use of identification and authentication mechanisms
10.2.6 Initialization of the audit logs
10.2.7 Creation and deletion of system-level objects
10.3 Record at least the following audit trail entries for each event, for all system components:
10.3.1 User identification
10.3.2 Type of event
10.3.3 Date and time
10.3.4 Success or failure indication
10.3.5 Origination of event
10.3.6 Identity or name of affected data, system component, or resource
10.4 Synchronize all critical system clocks and times.
10.5 Secure audit trails so they cannot be altered:
10.5.1 Limit viewing of audit trails to those with a job-related need.
10.5.2 Protect audit trail files from unauthorized modifications.
10.5.3 Promptly back up audit trail files to a centralized log server or media that is difficult to alter.
10.5.4 Copy logs for wireless networks onto a log server on the internal LAN.
10.5.5 Use file integrity monitoring and change detection software (such as Tripwire) on logs to ensure that existing log data cannot be changed without generating alerts (although new data being added should not cause an alert).
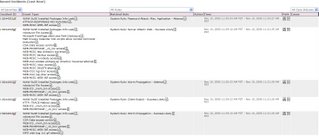
10.6 Review logs for all system components at least daily. Log reviews should include servers that perform security functions like IDS and authentication (AAA) servers (RADIUS, for example).
10.7 Retain your audit trail history for a period that is consistent with its effective use, as well as legal regulations. An audit history usually covers a period of at least one year, with a minimum of three months available online.
Cisco Recommendations to Requirement 10.
The PCI Data Security Standard (Requirement 10) states, “The presence of logs in all environments allows thorough tracking and analysis when something does go wrong. Determining the cause of a compromise is very difficult without a system activity log.”
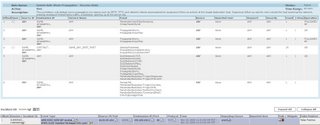
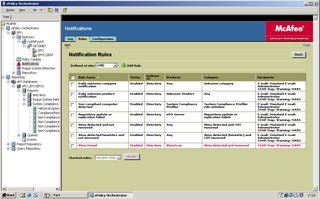
The Cisco Secure ACS Server in conjunction with CS-MARS can provide extensive information on access to network resources and cardholder data. Cisco Secure ACS authenticates, authorizes, and provides accounting information on usage parameters.
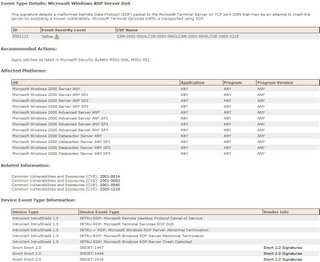
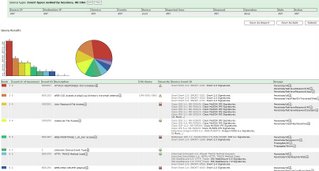
Cisco Secure Monitoring Analysis and Response System is a logging tool that stores all logs from a multitude of different vendors. In addition, CS-MARS is particularly strong at incident response once a security event occurs. For instance, it can provide early warning indicators, attack visualization, and mitigation recommendations to control security attacks. CS-MARS is a next-generation tool that meets all of these requirements and morel. The ability to visualize an attack and suggest methods
to stop its spread are indicative of the correlative intelligence that CS-MARS brings to a multi-vendor environment. In addition, sub-requirement 10.5.5 for file integrity checking of log files can be addressed with Cisco Security Agent.
Regularly Monitor and Test Networks
PCI Requirement 11: Regularly test security systems and processes.
Vulnerabilities are continually being discovered by hackers and researchers, and introduced by new software. Systems, processes, and custom software should be tested frequently to ensure security is maintained over time and through changes.
Sub-requirements:
11.1 Test security controls, limitations, network connections, and restrictions routinely to make sure they can adequately identify or stop any unauthorized access attempts. Where wireless technology is deployed, use a wireless analyzer periodically to identify all wireless devices in use.
11.2 Run internal and external network vulnerability scans at least quarterly and after any significant change in the network (new system component installations, changes in network topology, firewall rule modifications, or product upgrades, for example).
Note: External vulnerability scans must be performed by a scan vendor qualified by the PCI.
11.3 Perform penetration testing on network infrastructure and applications at least once a year and after any significant infrastructure or application upgrade or modification (operating system upgrade, subnetwork added to environment, Web server added to environment, for example).
11.4 Use network IDSs, host-based IDSs and IPSs to monitor all network traffic and alert personnel to suspected compromises. Keep all intrusion detection and prevention engines up to date.
11.5 Deploy file integrity monitoring to alert personnel to unauthorized modification of critical system or content files, and perform critical file comparisons at least daily (or more frequently if the process can be automated). Critical files do not necessarily contain cardholder data. For file integrity monitoring purposes, critical files are usually those that do not regularly change, but the modification of which could indicate a system compromise or risk of compromise. File integrity monitoring products usually come preconfigured with critical files for the related operating system. Other critical files, such as those for custom applications, must be evaluated and defined by the merchant or service provider.
Cisco Recommendations to PCI Requirement 11
The Cisco Customer Advocacy team is comprised of dedicated industry professionals with extensive expertise in conducting unbiased security posture assessments, penetration testing, and vulnerability scanning. Cisco would be pleased to engage this team in this process.
The Cisco Customer Advocacy team would help address sub-requirements 11.1 through 11.3.
The Cisco secure router already includes intrusion prevention capabilities. Customers can deploy IDS or IPS signatures to the router without the need for an additional IDS or IPS appliance. This helps address sub-requirement 11.4. This pervasive IDS/IPS solution will
control attacks for both wired and wireless users. In collaboration with CS-MARS, identified threats can be quickly stopped network wide.
When CS-MARS recognizes an attack, it will automatically propagate or enable the appropriate attack signature in every Cisco secure router equipped with the integrated intrusion prevention capability, quickly isolating and preventing the spread of the attack.
For customers requiring more powerful IDS/IPS appliances, Cisco recommends the Cisco IPS 4200 Series of sensor appliances. The Cisco IPS 4200 Series greatly increases the scalability and throughput of the security solution. Cisco also provides intrusion detection and prevention modules for the Cisco Catalyst 6500 Series. This illustrates the ability of Cisco security solutions to integrate natively into the infrastructure. The advanced intrusion prevention capabilities supported by Cisco IPS 4200 Series dedicated IPS appliances are also integrated into the Cisco ASA family.
The host-based Cisco Security Agent IPS tool can mitigate the threat from worms and viruses and can assist with file integrity checking as defined in Section 11.5.
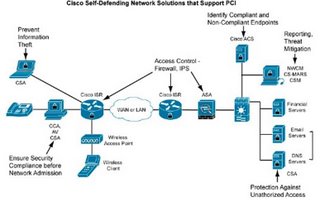
Managing Risk and Compliance with the Cisco Self-Defending Network
Managing Risk and Compliance with the Cisco Self-Defending Network - EMEA
Cisco Self-Defending Network Support for PCI Data Security Standard
Addressing the PCI Data Security Standard