 I`m not going to go through installing IAS, but theres plenty of guides to doing this on the web.
I`m not going to go through installing IAS, but theres plenty of guides to doing this on the web.Lets start by adding a new RADIUS Client...
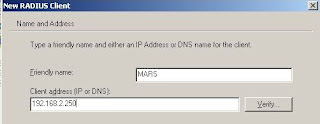 Now Click Next, and select Cisco for the Client-Vendor, and enter a shared key that the two devices will share for the authentication process.
Now Click Next, and select Cisco for the Client-Vendor, and enter a shared key that the two devices will share for the authentication process.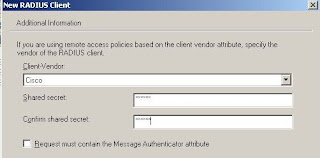 Next, we need to create a remote access policy. For ease, we will create a new one, and delete any existing predefined entries.
Next, we need to create a remote access policy. For ease, we will create a new one, and delete any existing predefined entries.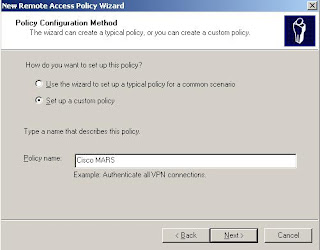 1. In the Internet Authentication Service window, click Remote Access Policies in the left pane.
1. In the Internet Authentication Service window, click Remote Access Policies in the left pane.2. In the right pane, right-click the default policy, and select Delete.
3. Right-click, and select New Remote Access Policy.
4. In the Remote Access Policy Wizard, click Next.
5. Click Set Up A Custom Policy, name it Cisco MARS, and click Next.
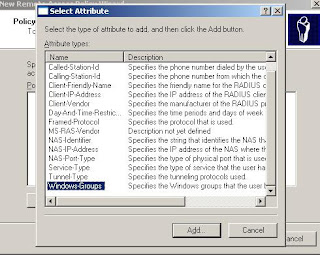
6. Click Add, select Windows-Groups, and click Add
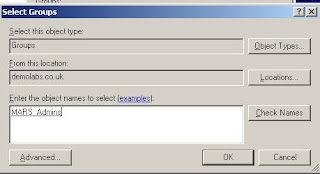
Specifiy a Windows group, and click OK. This takes you to the Policy Conditions screen of the New Remote Access Policy Wizard
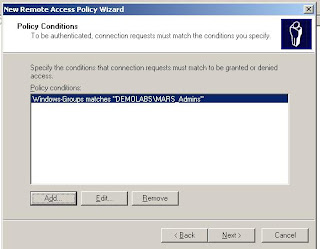
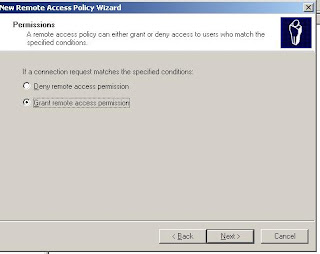
1. Click Next, select Grant Remote Access Permission, and click Next.
2. Click Edit Profile, and select the Authentication tab.
3. Only select the Unencrypted Authentication (PAP/SPAP) check box
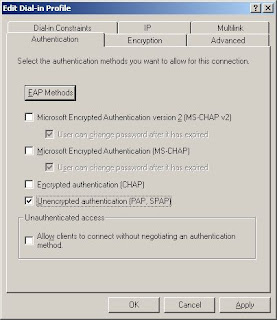
- Next, select the Advanced tab.
- Select Service-Type, and click Edit.
- In the Enumerable Attribute Information dialog box, select Login from the Attribute Value drop-down list.
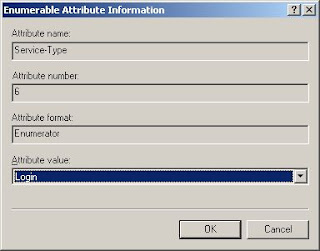
Back on the Advanced tab, select Framed-Protocol, and click Remove.
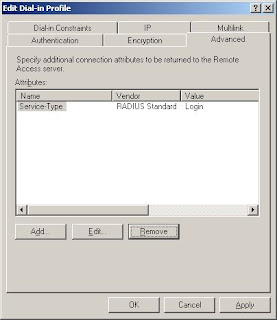
Click OK, and its done!
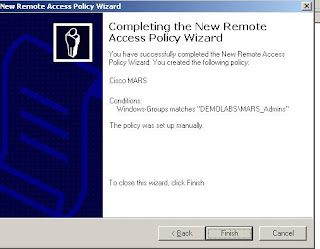 Oh, and one point, make sure you have allowed Dial-In rights, on the User, under AD Users and Computers.
Oh, and one point, make sure you have allowed Dial-In rights, on the User, under AD Users and Computers.Now the MARS Bit....
Now the first thing i would do is create user accounts in MARS, for the users you want AAA access. I know this seems weird, but you will see why later! Also make sure you create these case perfect to your windows accounts.
Once done, you can configure the MS IAS Server in MARS...
This is quite simple, go to Admin/Authentication Configuration...
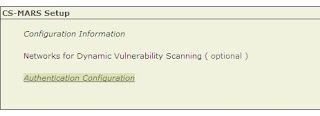
Now under AAA Server Configuration select ADD...

And, Add AAA Server on a new host..
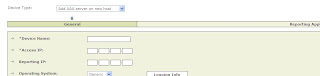
Fill in the IP`s etc, then click Next. Now click, ADD again for a Generic AAA Server..
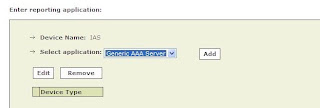
Now specify the name, and Shared Key we specified earlier in the IAS Config, along with the Radius Server ports. I used, 1812 and 1813.
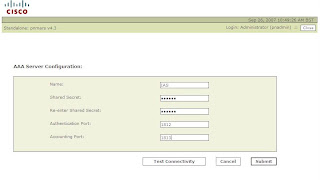 Now Click Test Connectivity, which will result, in either a Failure, if any of the parameters are wrong (especially the shared key), or success...
Now Click Test Connectivity, which will result, in either a Failure, if any of the parameters are wrong (especially the shared key), or success...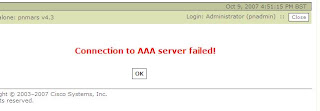
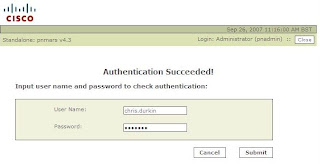 If Success, enter a windows user name and password to test the authentication process.
If Success, enter a windows user name and password to test the authentication process.Once done, we can then set MARS to use AAA for logins...
Under Admin/Authentication Configuration, specify the IAS Server as the authentication method, and optionally set a lock out.
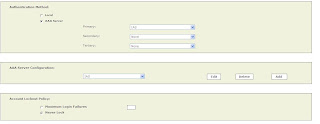 Once you click Submit, MARS will delete all the local User passwords you created earlier (except Admins).....
Once you click Submit, MARS will delete all the local User passwords you created earlier (except Admins).....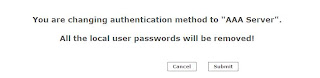
This will create an incident...
And thats it, all the MARS configuration done.
Now there are a couple of bits of note, to tell you about. To remove the IAS Server, you cannot do this via the normal Security and Monitor devices. If you try you will get this error...
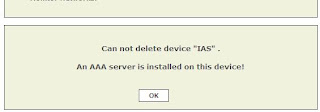
Instead, delete the IAS Server, via the Authentication Configuration screen.
Logging on the Microsoft IAS is pretty poor...
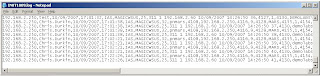 And these will be obviously stored on the Windows Box, and not MARS! Obviously with ACS and the agent, you can get the logs back into MARS, but Windows does not have a native Syslog engine.
And these will be obviously stored on the Windows Box, and not MARS! Obviously with ACS and the agent, you can get the logs back into MARS, but Windows does not have a native Syslog engine.So you could run a query with the PNMARS device, for account logins...
 Also a bug you should be aware about in the GUI when using AAA services, is that your user accounts may appear "locked", even if you do not use a Lock Out policy...
Also a bug you should be aware about in the GUI when using AAA services, is that your user accounts may appear "locked", even if you do not use a Lock Out policy...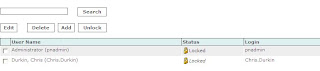
And err....
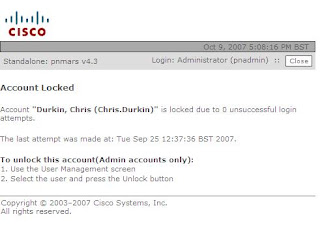
This does not effect the AAA function in anyway, and should be fixed in the next release.
Now this method worked fine in the lab, if you make a complete hash of the above dont blame me! :-)
In the next article i show you some CLI commands, to unlock user accounts.























